IoT Security Frameworks - Third Issue

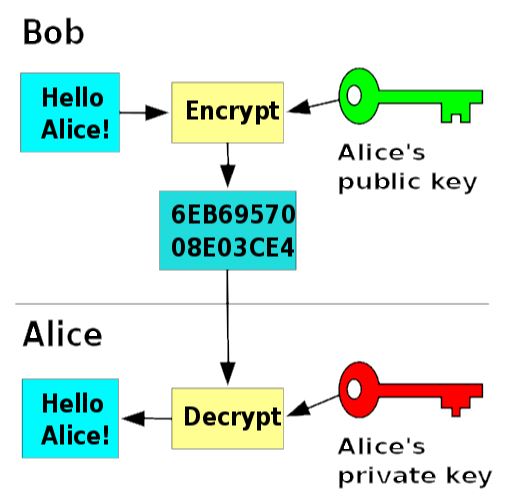
The cryptographic security methods we saw in the previous issues form an important component in IoT Security frameworks.
Security frameworks have as their main characteristics:
• Confidentiality: it disallows unwanted access to sensitive information.
• Integrity: it protects the transmitted data for unwanted modification or tampering.
• Availability: it is related to the ability of accessing the data when they are needed.
Typical attacks which can break these characteristics by exploiting vulnerabilities in the system are: RF interference, node tampering, jamming, man-in-the-middle attack, Denial of service attack, virus and worms, malicious scripts among many others.
The IoT world comprises small devices which are inherently insecure and the IoT Systems are vulnerable to attacks.
IoT Security Frameworks, in addition to being able to address Data anomaly detection, remote attestation or packet filtering issues in order to mitigate these complex attacks, should be scalable and support ease of testing.
If the IoT System is a complex one comprising large number of heterogeneous devices, detecting data anomalies and compromised nodes becomes very difficult and can be complicated if there are communication errors due to injection of malicious data.
Two generic IoT Frameworks which have made considerable efforts to tackle these issues are Internet of Things Architecture (IoT-A) or Core Platform of the Future Internet (FiWARE). While FiWARE implements a “security-by-design” paradigm with generic components (such as monitoring, identity, and confidentiality management, context security or secure storage), IoT-A uses a trust model involving Trust domains, Trust evaluation mechanisms, Behavior analysis and such security aspects.
The interaction of different security modules in the framework is ensured by establishing a trust relationship based on the authentication mechanism. The trust relationship is established using digital certificates, asymmetric keys or pre-shared symmetric keys, depending on the constraints of the devices involved.
“IoT security will be complicated by the fact that many “Things” use simple processors and OS…” - Gartner
Importantly, most of the good security algorithms developed so far - which typically involve large numbers and complex methods of handling them - find it challenging to fit into the current IoT or Industrial IoT hardware due to limitations related to size, power, speed, processing power, etc.
Moreover, since IoT allows sensor and actuator devices to communicate end-to-end through the system, the security techniques implemented by IoT end-nodes impact the rest of the involved devices.
With IoT devices and systems becoming more prevalent, paradoxically more and more consumers are concerned about the safety and security of the devices and there is more awareness of the security risks involved.
In conclusion, with the IoT market growing at an explosive rate, good developments in IoT Security and advancements are much needed and urgent.