IoT Security Frameworks
What’s something we all agree is very important for IoT? Security. In this series of Articles on IoT Security Frameworks, we look at the various security concepts & mechanisms, cryptographic principles and why security is very important for IoT.
As is the case with everything, for every positive there is an equal negative. While IoT gives us an infinite amount of possibilities to monitor, analyse and improve all aspects of our lives, it creates a huge risk for critical data to get into the wrong hands. With the increasing awareness of the safety hazards and privacy issues, it has become imperative for Cybersecurity to evolve and IoT devices and solutions to be equipped with up-to-date, fool proof security mechanisms.
This requires that the IoT product developers be armed with not only the security essentials, but a thorough knowledge of the various security concepts and mechanism, and the underlying cryptographic principles.
In its simplest form Cybersecurity is concerned with making sure that messages intended for a particular recipient cannot be read or modified by unauthorised people.
Cybersecurity further comprises 4 intertwined areas: secrecy, authentication, non-repudiation and integrity control.
- Secrecy has to do with keeping information out of the hands of unauthorized users. This is what usually comes to mind when people think about Cybersecurity.
- Authentication deals with determining whom you are talking to before revealing sensitive information - that is, verifying the claimed identity of the sender.
- Non-repudiation means that the sender cannot reject or disown the contents of the message sent. This ensures accountability for data shared by the sender.
- Integrity control is ensuring that the message received is really the one sent and not something that got modified in transit or was concocted.
Security Paradigms are broadly divided into Private key Systems (Triple DES, DES & AES) and Public key Systems (RSA and Diffe-Hellman & Digital Signature Algorithms).
Private key or Symmetric Cryptographic systems have been used for ages. In the Symmetric kind of system, the method followed is: the plaintext data to be transferred is encrypted using a secret Private key resulting in a Cipher text or the Encoded message, which is transmitted to the recipient who decrypts using the same Private key which was shared with him confidentially.
But this method gets compromised easily due to the difficulty of ensuring confidentiality in the first place – while sharing the Private key.
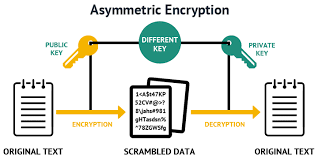
Asymmetric Cryptography aims to tackle this problem using a key pair: a Private key and a Public key.