IoT Security Frameworks - Second Issue
In this second instalment of IoT security Frameworks series, we look at Asymmetric cryptographic systems.
As we saw earlier, the problem with secret key cryptosystems was that the encryption and decryption keys were the same (or easily derived from the other) and that the keys had to be distributed to all users of the system. Since keys need to be protected from theft, the key distribution itself was a weak link in these systems.
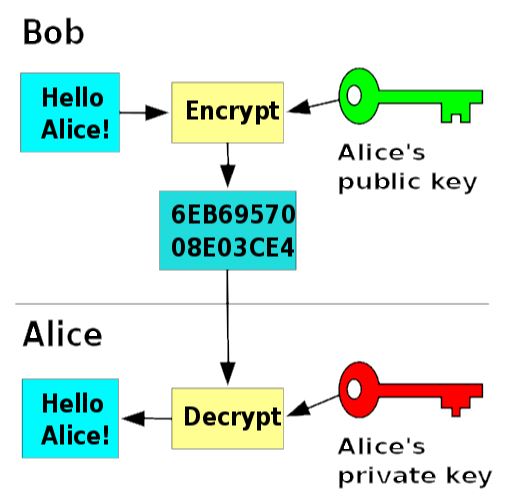
To solve this problem, The Asymmetric cryptographic or Public key system was proposed. In this system a key pair - a Private key that is known only to the sender and a public key which is shared with the receiver – is used. Here the encryption and decryption keys are different from each other and the decryption key cannot be derived from the encryption key.
In a public key cryptosystem, the encryption and decryption algorithms E and D are such that they meet the following requirements, where P is the plaintext:
• D(E(P)) = P;
• It is exceedingly difficult to deduce D from E;
• E cannot be broken by a chosen plaintext attack.
One of the early Asymmetric Cryptographic algorithms is RSA (named after its designers Rivest, Shamir and Adlernan) which satisfies all the above requirements.
This is a very good method and works as follows:
- Choose two large primes, p and q, typically greater than 10100.
- Compute n = p x q, and z = (p-1)(q-1).
- Choose a number d relatively prime to z.
- Find e such that e x d ≡ 1 (mod z).
Then divide the plaintext P (bit string) into blocks, so that each plaintext message P satisfies
0 <= P < n.
To encrypt, compute Ciphertext C = Pe(mod n). To decrypt C, compute P = Cd(mod n).
It can be proven that for all P in the specified range, the encryption and decryption functions are inverses. The public key consists of (e,n), the private key consists of (d,n).
The security of the method is based on the difficulty of factoring the product of two large primes. Because RSA uses very large primes, it is pretty slow when used to encrypt large volumes of data. Most RSA-based systems use public key cryptography for distributing one-time session keys for use with DES, IDEA or similar algorithms.
Though systems with RSA Encryption implementation have been around for decades, in addition to being slow, RSA is not very suitable when it comes to security of smaller devices and systems, especially IoT devices and systems. We will look at some other aspects of IoT Security Frameworks in the final issue.